A short thought piece on the potential cybersecurity risks of using public or unsecured Wi-Fi networks.
Please don’t assume I have considered all possible risks here, this is only one perspective. 😊
Intro
Networking is a complex and dynamic topic, and an understanding of key concepts involved is important to make security decisions based upon it.
As network traffic moves around a network like from a router to a computer and then to a specific program running on the computer, the traffic is ‘encapsulated’ from the sender and then ‘decapsulated’ by the receivers.
Network traffic is encapsulated so it can be interpreted by other computers. It is structured using a set of rules all computers on the network understand and these rules are called protocols.
Think of putting a letter in an envelope, it is a standard size and has an address written in a standard format and the data contained is in a language both parties understand; this is the protocol of sending a letter and computer networks operate is a very similar way.
Network traffic will be encapsulated multiple times, as data is decapsulated the next layer of encapsulation of revealed and the data is passed to a lower-level system –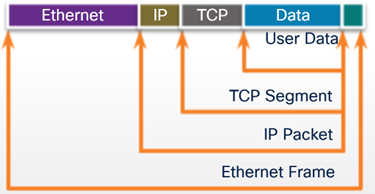
A VPN is a protocol which your computer can use to encapsulate all internet traffic in an encrypted stream to be decrypted at another location (essentially setting up a tunnel from one location to another with encryption) before being sent to the intended internet location.
When you connect to a Wi-Fi network, your computer is told information on where to go (the DNS server via DHCP) to convert website addresses (like google.com) to IP addresses. Your computer will accept the data the Wi-Fi network provides on how to look-up domains unless it is set manually and is assumed to be correct.
A VPN is considered more secure, as all data is encrypted before being sent over the Wi-Fi network. This way if an issue could be exploited in an encrypted protocol the computer uses to communicate, the data could not be read by the malicious Wi-Fi network operator as it is encapsulated/encrypted again by the VPN.
Network security has significantly improved in the last 5 years. Once, most protocols on the internet did not employ encryption, allowing anybody to eavesdrop on your computer communicating with low levels of sophistication and setup.
Now, modern and well-developed applications employ encrypted protocols to provide privacy.
Risks & Solutions
Eavesdropping by malicious Wi-Fi network operators – VPN mitigation
A VPN is recommended by official government advice when using public Wi-Fi, with a VPN internet traffic is encapsulated and encrypted strongly using one protocol which reduces the attack surface of your communications when connecting to public Wi-Fi; as without a VPN, there are many protocols your computer uses to communicate on the internet which allows more chance for poorly implemented protocols and unknown vulnerabilities in the protocols to cause security breaches.
The likelihood the type of attack a VPN mitigates is low as it requires high levels of sophistication.
DNS poisoning – Enable DNSSEC mitigation
DNS is arguably the weakest area when it comes to users accessing public Wi-Fi as it allows for malicious Wi-Fi network operators to redirect internet traffic to domains and preform man-in-the-middle attacks.
Manually setting the DNS server the computers look to for DNS and employing DNSSEC is the best solution.
Exploiting DNS is a fundamental part of many public Wi-Fi security breaches due to DNS being old and security focused by default.
Public Wi-Fi – 4G/5G mobile data mitigation
Government advice suggests using mobile data as an alternative to public Wi-Fi as this mitigates the risk of public Wi-Fi entirely.
Summary
The risk of using public Wi-Fi is lower than years past as networks have become more secure, risks do remain, and it is impossible to eliminate risk entirely with networks.
There are options available to mitigate different levels of risk which should be applied based off the risk tolerance of the organisation/user.

